DARKSURGEON - A Windows 10 Packer Project for Defenders

I’m happy to announce the alpha release of DARKSURGEON, a Windows 10 packer project to empower incident response, digital forensics, malware analysis, and network defense.
DARKSURGEON is designed to perform the following:
- Accelerate incident response, digital forensics, malware analysis, and network defense with a preconfigured Windows 10 environment complete with tools, scripts, and utilities.
- Provide a framework for defenders to customize and deploy their own programmatically-built Windows images using Packer and Vagrant.
- Reduce the amount of latent telemetry collection, minimize error reporting, and provide reasonable privacy and hardening standards for Windows 10.
If you haven’t worked with packer before, this project has a simple premise:
Provide all the tools you need to have a productive, secure, and private Windows virtual machine so you can spend less time tweaking your environment and more time fighting bad guys.
Development Principles
DARKSURGEON is based on a few key development principles:
- Modularity is key. Each component of the installation and configuration process should be modular. This allows for individuals to tailor their packer image in the most flexible way.
- Builds must be atomic. A packer build should either complete all configuration and installation tasks without errors, or it should fail. A packer image with missing tools is a failure scenario.
- Hardened out of the box. To the extent that it will not interfere with investigative workflows, all settings related to proactive hardening and security controls should be enabled. Further information on DARKSURGEON security can be found later in this post.
- Instrumented out of the box. To the extent that it will not interfere with investigative workflows, Microsoft Sysmon, Windows Event Logging, and osquery will provide detailed telemetry on host behavior without further configuration.
- Private out of the box. To the extent that it will not interfere with investigative workflows, all settings related to privacy, Windows telemetry, and error reporting should minimize collection.
Hardening
Hardening of the host must balance the needs of productivity with risk mitigation. DARKSURGEON pre-configured with scripts to enable either a High or Low Security mode, each tailored towards different workflows. Currently, only the low security mode is available for testing.
The default selection, Low Security, caters primarily to ephemeral use virtual machines (e.g. incident response or malware analysis, etc.)
Regardless of your selection, all default installations of DARKSURGEON have the following security features:
- Windows OS security guidelines are implemented.
- The latest Windows security patches are applied.
- Windows Secure Boot is Enabled.
- LLMNR is Disabled.
- NBT/NBT-NS is Disabled.
- WPAD is Disabled.
- Powershell v2 is Removed.
- SMB v1 is Disabled.
- Application handlers for commonly-abused file extensions are defanged (opened in notepad).
In Low Security mode, the following hardening features are present:
- Windows Defender Anti-Virus (WDAV) is enabled with hourly auto-updates.
- Windows Defender Anti-Virus Real-Time Scanning is Disabled.
- Windows Defender Anti-Virus Cloud Checks are Disabled.
- Windows Defender SmartScreen is Disabled.
- Windows Defender Credential Guard is Disabled.
- Windows Defender Exploit Guard is Disabled.
- Windows Defender Exploit Guard Attack Surface Reduction (ASR) is Disabled.
- Windows Defender Application Guard is Disabled.
- Windows Defender Firewall is Enabled with default rules.
Telemetry
Whether analyzing unknown binaries or working on sensitive projects, endpoint telemetry powers detection and response operations. DARKSURGEON comes pre-configured with the following telemetry sources available for analysis:
- Windows Event Log Auditing is enabled. (Palantir Windows Event Forwarding Guidance).
- Windows Powershell Auditing is enabled. (Palantir Windows Event Forwarding Guidance).
- Sysinternals Sysmon is installed and configured. (SwiftonSecurity Ruleset)
Privacy
Your operational environment contains some of the most sensitive data from your network, and it’s important to safeguard that from prying eyes. DARKSURGEON implements the following strategies to maximize privacy without hindering workflows:
- Windows 10 telemetry settings are configured to minimize collection.
- Cortana, diagnostics, tracking, and other services are disabled.
- Windows Error Reporting (WER) is disabled.
- Windows Timeline, shared clipboard, device hand-off, and other synchronize-by-default applications are disabled or neutered.
- Microsoft Guidance for reducing telemetry and data collection has been implemented.
Base Tooling
Out of the box, DARKSURGEON comes equipped with tools, scripts, and binaries to make your life as a defender easier. The following are a non-exhaustive listing of the various categories and tools present in the project:
Android Analysis: Tools, scripts, and binaries focused on android analysis and reverse engineering. Examples include:
- APKTool
Blue Team: Tools, scripts, and binaries focused on blue team, network defense, and alerting/detection development. Examples include:
- Atomic Red Teaming (Red Canary)
- Bloodhound / Sharphound
- CimSweep
- Dumpsterfire
- EndGame Red Team Automation (RTA)
- Kansa
- Invoke-ATTACKAPI
- Posh-Sysmon
- PowerForensics
- Yara
Debuggers: Tools, scripts, and binaries for debugging binary artifacts. Examples include:
- Ollydbg
- x64dbg
- Windbg
Disassemblers: Tools, scripts, and binaries for disassembling binary artifacts. Examples include:
- IDA 7 (Demo)
- Binary Ninja (Demo)
DotNet Analysis: Tools, scripts, and binaries for performing analysis of DotNet artifacts. Examples include:
- DNSpy
- DotPeek
Flash Analysis: Tools, scripts, and binaries for performing analysis of flash artifacts. Examples include:
- FFDec
Forensic Analysis: Tools, scripts, and binaries for performing forensic analysis on application and operating system artifacts. Examples include:
- Amcache Parser
- AppCompatCache Parser
- Shellbags Explorer
- TSK (The Sleuthkit)
- Volatility
Hex Editors: Hex editing software. Examples include:
- HxD
- 010 Editor
Java Analysis: Tools, scripts, and binaries for performing analysis of Java artifacts. Examples include:
- JD-GUI
- Dex2JAR
Network Analysis: Tools, scripts, and binaries for performing analysis of network traffic and protocols. Examples include:
- Burp Free
- FakeNet-NG
- Wireshark
PE Analysis: Tools, scripts, and binaries for performing analysis of PE artifacts. Examples include:
- ExplorerSuite (CFF Explorer)
- PEStudio
- PEview
Powershell Modules: Administration, productivity, and support modules for Powershell. Examples include:
- Active Directory (RSAT)
- Azure Management
- Pester
Python Libraries: Administration, productivity, and support libraries for Python. Examples include:
- OLETools
- Passivetotal
- PEFile
- PyCryptodome
- Scapy
- Shodan
- Vivisect
- Yara-Python
Red Team: Tools, scripts, and binaries focused on red team, network exploitation, and alerting/detection development. Examples include:
- Grouper
- Inveigh
- PowerupSQL
- PSAttack
- Responder
Remote Management: Administration, productivity, and support modules for remote management of systems and applications. Examples include:
- AWS Command Line (AWSCLI)
- Remote Server Administration Tools (RSAT)
Utilities: Administration, productivity, and support utilities. Examples include:
- API Monitor
- Chocolatey
- Cyber Chef
- Windows Subsystem for Linux (WSL)
- Winlogbeat
Visual Basic Analysis: Tools, scripts, and binaries for performing analysis of Visual Basic artifacts. Examples include:
- VBDecompiler
Building DARKSURGEON
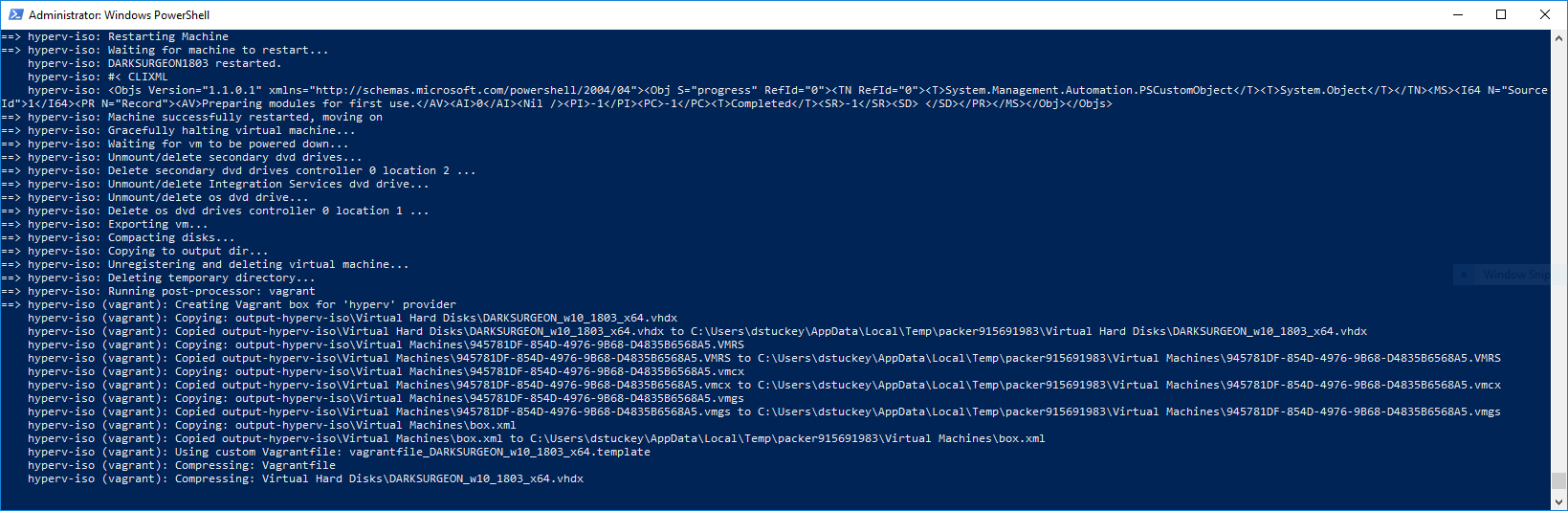
Build Process
DARKSURGEON is built using the HashiCorp application packer. The total build time for a new instance of DARKSURGEON is around 2–3 hours.
- Packer creates a new virtual machine using the DARKSURGEON JSON file and your hypervisor of choice (e.g. Hyper-V, Virtualbox, VMWare).
- The answers.iso file is mounted inside the DARKSURGEON VM along with the Windows ISO. The answers.iso file contains the unattend.xml needed for a touchless installation of windows, as well as a powershell script to configure Windows Remote Management (winrm).
- Packer connects to the DARKSURGEON VM using WinRM and copies over all files in the helper-scripts and configuration-files directory to the host.
- Packer performs serial installations of each of the configured powershell scripts, performing occasional reboots as needed.
- When complete, packer performs a sysprep, shuts down the virtual machine, and creates a vagrant box file. Additional outputs may be specified in the post-processors section of the JSON file.
Setup
Note: Hyper-V is currently the only supported hypervisor in this alpha release. VirtualBox and VMWare support are forthcoming.
- Install packer, vagrant, and your preferred hypervisor on your host.
- Download the repository contents to your host.
- Download a Windows 10 Enterprise Evaluation ISO (1803).
- Move the ISO file to your local DAKRSURGEON repository.
- Update the DARKSURGEON.json file with the Windows ISO SHA1 hash and file name.
- (Optional) Execute the powershell script New-DARKSURGEONISO.ps1 to generate a new answers.iso file. There is an answers ISO file included in the repository but you may re-build this if you don’t trust it, or you would like to modify the unattend files:
powershell.exe New-DARKSURGEONISO.ps1 - Build the recipe using packer:
packer build -only=[hyperv-iso|vmware|virtualbox] .\DARKSURGEON.json
Configuring DARKSURGEON
DARKSURGEON is designed to be modular and easy to configure. An example configuration is provided in the DARKSURGEON.json file, but you may add, remove, or tweak any of the underlying scripts.
Have a custom CA you need to add? Need to add a license file for IDA? No problem. You can throw any files you need in the configuration-files directory and they’ll be copied over to the host for you.
Want to install a custom package, or need some specific OS tweaks? No worries. Simply make a new powershell script (or modify an existing one) in the configuration-scripts directory and add it as a build step in the packer JSON file.
Using DARKSURGEON
Note: Hyper-V is currently the only supported hypervisor in this alpha release. VirtualBox and VMWare support are forthcoming.
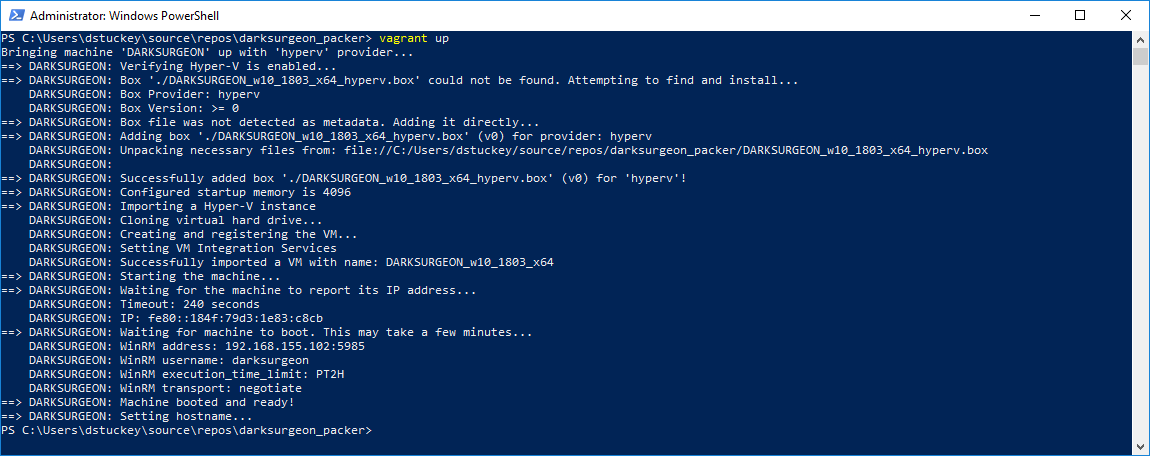
Once DARKSURGEON has successfully built, you’ll receive an output vagrant box file. The box file contains the virtual machine image and vagrant metadata, allowing you to quickly spin up a virtual machine as needed.
- Install vagrant and your preferred hypervisor on your host.
- Navigate to the DARKSURGEON repository (or the location where you’ve saved the DARKSURGEON box file).
- Perform a vagrant up:
vagrant up
Vagrant will now extract the virtual machine image from the box file, read the metadata, and create a new VM for you.
Want to kill this VM and get a new one? Easy, just perform the following: vagrant destroy && vagrant up
Once the DARKSURGEON virtual machine is running, you can login using one of the two local accounts:
Note: These are default accounts with default credentials. You may want to consider changing the credentials in your packer build.
Administrator Account:
Username: darksurgeon
Password: darksurgeon
Local User Account:
Username: unprivileged
Password: unprivileged
If you’d rather not use vagrant, you can either import the VM image manually, or look at one of the many other post-processor options provided by packer.
Next Steps
Ready to get started? Just head over to the GitHub Repository and download the project.
Contributing
Contributions, fixes, and improvements can be submitted directly against this project as a GitHub issue or pull request. Tools will be reviewed and added on a case-by-case basis.
Further Reading and Acknowledgements
This project stands on the shoulders of giants, and I cannot properly thank all of the original authors for their work, contributions, and inspiration.
- Joe Fitzgerald for pioneering Windows packer projects.
- The FLARE team at FireEye for their awesome work on the chocolatey packages and repository for the FLAREVM project.
- Chris Long for his awesome work on DetectionLab and the packer CI pipeline.
- All of the authors, chocolatey package maintainers, and tool writers that made this possible.
- Friends and colleagues for challenging me to finally open source this project.
